Securing your Mail Services with SSL

Two weeks ago I explained how to setup Postfix and Dovecot on Debian Etch. This post explains how to add some security against unwanted sniffers through SSL/TLS. With the explained setup all IMAP traffic will be encrypted and some of the SMTP traffic when supported by the other side.
Encryption, Trust and Certificates
SSL stands for Secure Sockets Layer and has two tasks:
- It adds end-to-end encryption to your communication making intermediate eavesdropping (nearly) impossible
- It adds trust by giving you a way to be sure with whom you communicate
You are probably familiar with both uses from internet shopping. SSL makes sure your credit card data can not be sniffed and let's you know you are really talking to your shop of choice.
The trust part is very important when dealing with things like online shopping. Because you can not easily know if a website's certificate is valid, SSL has a way to delegate trust. This is done by trusting certificate authorities (CA). If a trusted CA signed the certificate shown by the website, then you can trust the certificate itself 1).
For our mail setup, the trust part is less important. We want to get mails from everybody, regardless if they support SSL or not. But if supported it should be encrypted during transport. This will not be perfect, there may still be multiple points where you mail could be intercepted unencrypted and because of the missing trust part this is open to Man-in-the-middle attacks.
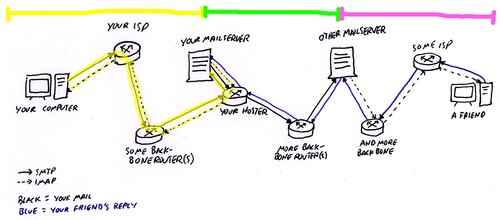
A look at the following image should explain what parts are involved in mail communication. At each router and server not controlled by you, a possible eavesdropper could read your mail. The setup described below will secure the yellow part. The green and pink parts are secured only when supported by the “other mail server” and “your friend”.
If you need 100% secure and trustable mails other mechanisms like GPG are a far better choice.
But still, each bit helps 
The SSL Certificate
There are several ways to get a SSL certificate:
- You may already got one with your hosting plan
- You can buy one from various sources
- You can get one for free from cacert.org
- You can create your own one
I'll describe how to do the last one here.
Creating a Self Signed Certificate
As always you need to install the needed packages2).
#> apt-get install openssl
As said above, trust isn't most important for this article. This allows us to eliminate the need for a certificate authority when creating a certificate to use3). Instead a so called self signed certificate will be used.
First a private key needs to be created using the openssl tool.
#> openssl genrsa -out serverKey.pem 1024
Next a certificate request will be created.
#> openssl req -new -key serverKey.pem -out serverCert.req
You need to watch one important thing for the certificate request: your common name must match the mail server host name. In our example this was mail.alice.xom
Country Name (2 letter code) [AU]:US State or Province Name (full name) [Some-State]:NY Locality Name (eg, city) []:New York City Organization Name (eg, company) [Internet Widgits Pty Ltd]:Alice and Friends Organizational Unit Name (eg, section) []: Common Name (eg, YOUR name) []:mail.alice.xom Email Address []:postmaster@alice.xom Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Just hit Enter for the challenge password to leave it empty.
Finally the request is signed by our own private key, creating the certificate.
#> openssl x509 -req -days 1825 -in serverCert.req -signkey serverKey.pem -out serverCert.pem
Move Certs and Keys
The key and certificate files should be placed in certain standard locations and the private key needs to be secured from everyone except root:
#> mv serverCert.pem /etc/ssl/certs/ #> mv serverKey.pem /etc/ssl/private/ #> chmod 400 /etc/ssl/private/serverKey.pem
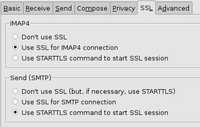
(Re)Configuring Dovecot
Just change the protocols line from imap to imaps and add the paths to your files
protocols = imaps ssl_cert_file = /etc/ssl/certs/serverCert.pem ssl_key_file = /etc/ssl/private/serverKey.pem
Restart dovecot and configure your mail client to use an SSL connection on Port 993.
#> /etc/init.d/dovecot restart
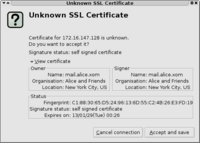
The first time you connect, you should be asked to verify and accept the certificate.
(Re)Configuring Postfix
For dovecot we changed the whole protocol to SSL only on a different port. This is not possible for SMTP because other mail servers expect it to answer on port 25. Instead we will use TLS. TLS is an extension to SSL which allows supporting clients to enable encryption within the existing protocol.
This is done by adding the following section to /etc/postfix/main.cf.
# Enable TLS support
smtpd_use_tls = yes
smtpd_tls_key_file = /etc/ssl/private/serverKey.pem
smtpd_tls_cert_file = /etc/ssl/certs/serverCert.pem
smtpd_tls_loglevel = 1
smtpd_tls_received_header = yes
smtp_use_tls = yes
smtp_tls_note_starttls_offer = yes
smtp_tls_key_file = /etc/ssl/private/serverKey.pem
smtp_tls_cert_file = /etc/ssl/certs/serverCert.pem
smtp_tls_loglevel = 1
smtpd_tls_session_cache_database = btree:${queue_directory}/smtpd_scache
smtp_tls_session_cache_database = btree:${queue_directory}/smtp_scache
Again, restart Postfix and configure your mail client to use TLS and accept the certificate when asked for.
#> /etc/init.d/postfix restart
Postfix will now use encryption for all communication between your mail client and the mail server. Additionally it will try to establish encrypted TLS connections to all mail servers it speaks to - if they support it.